Essential Guide To Unlocking The Power Of Tor
What is Tor? Tor is a free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis.
Tor is intended to protect the personal privacy of users, as well as their right to freedom of expression, by preventing Internet activity from being traced back to the user. This includes users' visited websites, online posts, instant messages, and other communications. Tor's use is not limited to protecting individuals; it can also be used to protect against a compromised network, and it is often used by journalists, activists, and law enforcement officers.
Tor was originally developed by the United States Naval Research Laboratory for the purpose of protecting U.S. intelligence communications online. The technology was then transferred to The Tor Project, a non-profit organization, which continues to develop and maintain Tor.
- Latest Josh Gates Breaking News Exploring The Unknown
- Barry Williams Life Career Net Worth And Marriage Unveiled
Tor
There are several key aspects to Tor that make it an effective tool for protecting privacy and anonymity online:
- Encryption: Tor encrypts all traffic that passes through its network, making it difficult for eavesdroppers to intercept and read.
- Anonymity: Tor uses a distributed network of relays to route traffic in a way that makes it difficult to trace back to the user.
- Free and open-source: Tor is free to download and use, and its source code is available to anyone who wants to inspect it or contribute to its development.
Tor and Privacy
Tor is a powerful tool for protecting privacy online. It can be used to protect against a variety of threats, including:
- Government surveillance: Tor can be used to protect against government surveillance by encrypting traffic and making it difficult to trace back to the user.
- Corporate surveillance: Tor can be used to protect against corporate surveillance by preventing companies from tracking users' online activity.
- Malware and phishing attacks: Tor can be used to protect against malware and phishing attacks by preventing malicious actors from accessing users' personal information.
Tor and Freedom of Expression
In addition to protecting privacy, Tor can also be used to protect freedom of expression. Tor allows users to access websites and online content that may be blocked or censored in their country. This can be especially important for journalists, activists, and others who need to access information that is not freely available.
- Astonishing Wealth Of Hugh Jackman Uncovering His Net Worth
- The Unforgettable Performances Of Morgan Freeman On Screen And Beyond
Tor
Despite its many benefits, Tor is not without its challenges and limitations. Some of the challenges associated with Tor include:
- Slow speeds: Tor can be slow because it encrypts traffic and routes it through a distributed network of relays.
- Network congestion: Tor can be congested during peak usage times, which can further slow down speeds.
- Not foolproof: Tor is not foolproof, and it is possible for users to be deanonymized if they make mistakes or if their computer is compromised.
Conclusion
Tor is a powerful tool for protecting privacy and freedom of expression online. However, it is important to be aware of the challenges and limitations associated with Tor before using it. Overall, Tor is a valuable tool for anyone who wants to protect their privacy and anonymity online.
Tor
Tor is a free and open-source software for enabling anonymous communication. It is a powerful tool for protecting privacy and freedom of expression online. Tor has many key aspects that make it an effective tool for these purposes.
- Encryption: Tor encrypts all traffic that passes through its network, making it difficult for eavesdroppers to intercept and read.
- Anonymity: Tor uses a distributed network of relays to route traffic in a way that makes it difficult to trace back to the user.
- Free and open-source: Tor is free to download and use, and its source code is available to anyone who wants to inspect it or contribute to its development.
- Protects privacy: Tor can be used to protect against government surveillance, corporate surveillance, and malware and phishing attacks.
- Protects freedom of expression: Tor allows users to access websites and online content that may be blocked or censored in their country.
- Slow speeds: Tor can be slow because it encrypts traffic and routes it through a distributed network of relays.
- Network congestion: Tor can be congested during peak usage times, which can further slow down speeds.
- Not foolproof: Tor is not foolproof, and it is possible for users to be deanonymized if they make mistakes or if their computer is compromised.
These are just some of the key aspects of Tor. It is a complex and powerful tool that can be used to protect privacy and freedom of expression online. However, it is important to be aware of the challenges and limitations associated with Tor before using it.
Encryption
Encryption is essential for protecting privacy and security online. Tor uses multiple layers of encryption to protect user traffic from eavesdropping and surveillance. This makes it very difficult for attackers to intercept and read data that is sent over the Tor network.
- Secure communication: Tor encrypts all communication between users and websites, making it impossible for eavesdroppers to intercept and read the contents of the communication.
- Protection against traffic analysis: Tor encrypts all traffic that passes through its network, making it difficult for attackers to analyze traffic patterns and identify users.
- Protection against man-in-the-middle attacks: Tor uses encryption to protect against man-in-the-middle attacks, in which an attacker intercepts communication between two parties and impersonates one of them.
Encryption is a critical component of Tor's security and privacy protections. It allows users to communicate and browse the web anonymously and securely, without fear of being eavesdropped on or tracked.
Anonymity
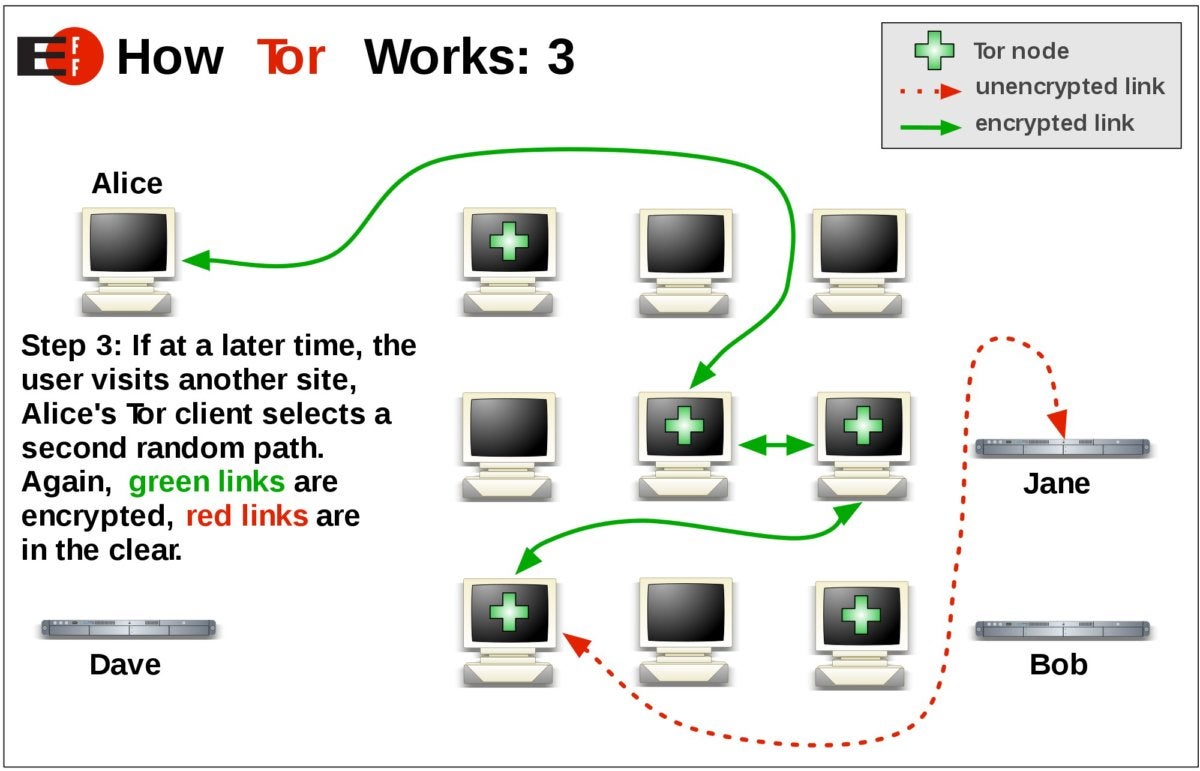
Anonymity is one of the most important features of Tor. It allows users to browse the web and communicate online without being tracked or identified. Tor achieves anonymity by using a distributed network of relays to route traffic in a way that makes it difficult to trace back to the user.
- Distributed network: Tor's network is made up of thousands of volunteer relays that are located all over the world. When a user connects to Tor, their traffic is routed through a series of these relays, making it difficult for anyone to track the user's activity back to their original IP address.
- Encryption: Tor encrypts all traffic that passes through its network, making it impossible for eavesdroppers to intercept and read the contents of the communication.
- Circuit-based connections: Tor uses circuit-based connections to route traffic through its network. This means that each time a user connects to a website, a new circuit is created. The circuit is made up of a series of relays that are chosen randomly. This makes it even more difficult for anyone to track the user's activity back to their original IP address.
Tor's anonymity features make it a valuable tool for protecting privacy and freedom of expression online. It can be used to protect against government surveillance, corporate surveillance, and other threats to privacy.
Free and open-source
Tor's free and open-source nature is one of its key strengths. It allows anyone to download, use, and modify the software, which promotes transparency and accountability. This is in contrast to proprietary software, which is developed and controlled by a single company or organization.
- Transparency: Because Tor is open-source, anyone can inspect the code and verify that it is not being used for malicious purposes. This helps to build trust and confidence in the software.
- Security: Open-source software is often more secure than proprietary software because it is constantly being reviewed and audited by a community of developers. This helps to identify and fix security vulnerabilities.
- Customization: Because Tor is open-source, users can modify the software to meet their specific needs. This can be useful for users who want to add additional features or functionality to Tor.
- Community development: Tor's open-source nature has led to a large community of developers who contribute to the project. This community helps to maintain and improve Tor, and it also provides support to users.
Tor's free and open-source nature is essential to its mission of protecting privacy and freedom of expression online. It allows anyone to use and contribute to the software, and it helps to ensure that Tor is transparent, secure, and customizable.
Protects privacy
Tor is a powerful tool for protecting privacy online. It can be used to protect against a variety of threats, including government surveillance, corporate surveillance, and malware and phishing attacks.
- Government surveillance: Tor can be used to protect against government surveillance by encrypting traffic and making it difficult to trace back to the user. This can be especially important for journalists, activists, and others who need to protect their communications from being intercepted by the government.
- Corporate surveillance: Tor can be used to protect against corporate surveillance by preventing companies from tracking users' online activity. This can be important for anyone who is concerned about their privacy and does not want their online activity to be tracked and used for advertising or other purposes.
- Malware and phishing attacks: Tor can be used to protect against malware and phishing attacks by preventing malicious actors from accessing users' personal information. This can be important for anyone who wants to protect their computer from being infected with malware or from being phished.
Tor is a valuable tool for anyone who wants to protect their privacy online. It is free to download and use, and it is easy to set up. If you are concerned about your privacy, Tor is a good option to consider.
Protects freedom of expression
Tor is a powerful tool for protecting freedom of expression online. It allows users to access websites and online content that may be blocked or censored in their country. This is especially important for journalists, activists, and others who need to access information that is not freely available.
- Circumventing censorship: Tor can be used to circumvent censorship by allowing users to access websites that are blocked in their country. This can be important for people who live in countries with authoritarian governments that restrict access to certain websites and online content.
- Accessing news and information: Tor can be used to access news and information that is not available in the user's country. This can be important for people who live in countries where the media is controlled by the government or where there is a lack of independent media.
- Protecting whistleblowers and activists: Tor can be used to protect whistleblowers and activists who need to communicate with journalists or other outside parties without being tracked or identified. This can be important for people who are exposing corruption or other wrongdoing.
Tor is a valuable tool for protecting freedom of expression online. It allows users to access information and communicate with others without fear of being censored or tracked. This is essential for a free and open society.
Slow speeds
Tor's slow speeds are a trade-off for the privacy and anonymity it provides. The encryption process and the use of multiple relays can add latency to the network. However, Tor's speed is constantly being improved. In recent years, Tor has made significant progress in reducing its latency, and it is now usable for many everyday activities, such as browsing the web, checking email, and instant messaging.
There are a number of things that users can do to improve their Tor speed. One is to use a faster Tor relay. Another is to use a bridge, which is a server that helps to connect users to the Tor network. Bridges can be faster than regular Tor relays, but they are also more likely to be blocked by censors.
Despite its slow speeds, Tor remains a valuable tool for protecting privacy and anonymity online. Users who are concerned about their privacy should consider using Tor, even if it means sacrificing some speed.
Network congestion
Tor's network can become congested during peak usage times, which can further slow down speeds. This is because Tor is a popular service, and many people use it at the same time. When the network is congested, it can take longer for traffic to be routed through the network, which can lead to slower speeds for users.
- Increased latency: When the Tor network is congested, it can increase latency, which is the time it takes for data to travel from one point to another. This can make it difficult to use Tor for real-time applications, such as video conferencing or online gaming.
- Reduced bandwidth: When the Tor network is congested, it can also reduce bandwidth, which is the amount of data that can be transferred over the network in a given amount of time. This can make it difficult to download large files or stream videos.
- Unreliable connections: When the Tor network is congested, it can also lead to unreliable connections. This means that connections may be dropped or interrupted, which can make it difficult to use Tor for applications that require a stable connection.
There are a number of things that users can do to reduce the impact of network congestion on their Tor speeds. One is to use a faster Tor relay. Another is to use a bridge, which is a server that helps to connect users to the Tor network. Bridges can be faster than regular Tor relays, but they are also more likely to be blocked by censors.
Despite the challenges of network congestion, Tor remains a valuable tool for protecting privacy and anonymity online. Users who are concerned about their privacy should consider using Tor, even if it means sacrificing some speed.
Not foolproof
Tor is a powerful tool for protecting privacy and anonymity online, but it is important to remember that it is not foolproof. There are a number of ways that users can be deanonymized if they make mistakes or if their computer is compromised.
One way that users can be deanonymized is if they use Tor with a vulnerable browser or operating system. For example, if a user is using Tor with an outdated version of Firefox, it is possible for an attacker to exploit a vulnerability in the browser to deanonymize the user.
Another way that users can be deanonymized is if they visit malicious websites. For example, if a user visits a website that has been compromised by an attacker, the attacker may be able to use the website to deanonymize the user.
Finally, users can also be deanonymized if their computer is compromised by malware. For example, if a user's computer is infected with a keylogger, the malware may be able to record the user's Tor traffic and deanonymize the user.
It is important to be aware of the risks of using Tor and to take steps to protect yourself from being deanonymized. Some of the steps that you can take to protect yourself include:
- Using an up-to-date browser and operating system
- Being careful about the websites that you visit
- Using a firewall and antivirus software
- Being aware of the risks of using Tor
By taking these steps, you can help to protect yourself from being deanonymized and maintain your privacy and anonymity online.
Frequently Asked Questions about Tor
Tor is a free and open-source software for enabling anonymous communication. It is a powerful tool for protecting privacy and freedom of expression online. However, there are some common questions and misconceptions about Tor that we will address in this FAQ.
Question 1: Is Tor illegal?
No, Tor is not illegal. It is legal to download, use, and distribute Tor in most countries. However, there are some countries where Tor is blocked or restricted. For example, Tor is blocked in China and Iran.
Question 2: Is Tor safe?
Tor is generally safe to use. However, it is important to be aware of the risks involved in using Tor. For example, Tor can slow down your internet connection and it is not foolproof. It is possible to be deanonymized if you make mistakes or if your computer is compromised.
Overall, Tor is a valuable tool for protecting privacy and freedom of expression online. However, it is important to be aware of the risks involved in using Tor and to take steps to protect yourself.
Conclusion
Tor is a free and open-source software for enabling anonymous communication. It is a powerful tool for protecting privacy and freedom of expression online. Tor encrypts all traffic that passes through its network, making it difficult for eavesdroppers to intercept and read. Tor also uses a distributed network of relays to route traffic in a way that makes it difficult to trace back to the user. This makes Tor a valuable tool for journalists, activists, and others who need to protect their privacy and anonymity online.
However, it is important to be aware of the challenges and limitations associated with Tor. Tor can be slow, and it is not foolproof. It is possible to be deanonymized if you make mistakes or if your computer is compromised. Overall, Tor is a valuable tool for protecting privacy and freedom of expression online. However, it is important to use Tor safely and to be aware of the risks involved.
Article Recommendations
- Investigating The Life And Work Of Hollywood Icon Anissa Jones
- Meet Jeffreyean Morgan The Heartthrob Of Greys Anatomy


Detail Author:
- Name : Jorge Cummerata
- Username : ellsworth55
- Email : briana.lesch@yahoo.com
- Birthdate : 1989-06-26
- Address : 41268 Schamberger River Suite 148 North Dejahborough, VT 21499-9359
- Phone : 1-601-891-1080
- Company : Stiedemann-Homenick
- Job : Forestry Conservation Science Teacher
- Bio : A ex est numquam sit autem. Quidem sunt repellendus facere ut sunt maiores id. Quia cum quia quas.
Socials
linkedin:
- url : https://linkedin.com/in/jesus.champlin
- username : jesus.champlin
- bio : Porro earum modi odit non qui sunt est eos.
- followers : 4362
- following : 135
facebook:
- url : https://facebook.com/jesuschamplin
- username : jesuschamplin
- bio : Quae eligendi non ullam consequatur quas doloremque.
- followers : 3284
- following : 2022
instagram:
- url : https://instagram.com/jesuschamplin
- username : jesuschamplin
- bio : Dolorem ut quam eum ut excepturi qui rerum. Praesentium autem id error aliquam nobis.
- followers : 5338
- following : 2823